
Industrial organizations
are looking for solutions to maintain their operations in order to keep a
competitive position as the global supply chain continues to be disrupted.
Organizations are using cutting-edge networking technology to track, transmit,
and eventually turn data into insightful knowledge to quicken the digitization
process. Furthermore, connected equipment exposes business owners to new
cybersecurity vulnerabilities, demanding component-level security skills to
control these threats. Manufacturers will implement connected technology in
products to increase reliability, leading to an increase in uptime and more
efficient maintenance supply chains.
As more assets are
connected and new technologies are routinely included in products, networking
components are becoming more and more crucial. In order to guarantee data
accessibility, integrity, and security, industrial companies that wish to take
advantage of the expanded services that may be provided by connecting more
devices should indeed keep in mind that they are doing this securely and in
line with regulations and guidelines.
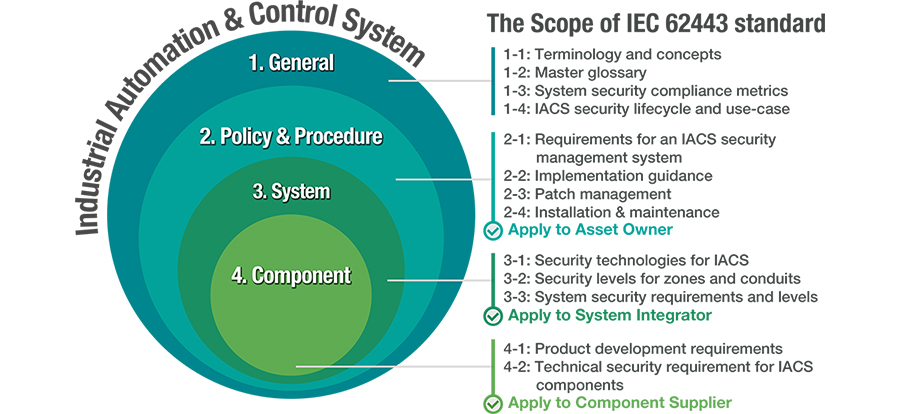
IEC 62443 in a Nutshell
The security framework for industrial control systems is outlined by a number of standards, and among them is the IEC 62443 standard, the most widely used and regularly adopted one. IEC 62443 contains guidelines that specify how to develop electronically secure IACS for various network components. This standard also contains instructions for people who manage automation and carry out other tasks on the network, and the IEC 62443 standard's device subsection is now often mandated by the system integrators.
Make the network more secure
- A defined set of policies and a security management system
To assist owners in obtaining the most recent information about
the security posture, visualization software must be deployed once the policies
and security management system have been confirmed.
- Defending IACS networks from cyberattacks with defense-in-depth
Partitioning systems into zones and conduits is recommended by a defense-in-depth strategy because it reduces risks to amounts that a business can tolerate.
Network operators must make sure that the security level allocated to each zone and conduit is followed. Through the utilization of industrial secure routers, VPNs, and wireless access solutions for industrial automation, the defense-in-depth strategy could be implemented with either physical or logical segregation. Also, some networking capabilities, like ACLs (Access control lists), could assist in partitioning networks to achieve different security levels.
- Embedded security features in hardened devices
Asset owners and SIs can guarantee that their systems reach the
required security standards by using the building blocks with built-in
security.
Requirements for Automation Industry Regulations in IEC 62443-4-2
Different subsections of
IEC 62443 relate to different responsibilities. This subsection, which
establishes requirements for component suppliers under IEC 62443-4-2, is
becoming more and more important as SIs constantly demand compliance. The
foundational requirements, such as identifiers, authenticators, password-based
authentication, public key authentication, data integrity, privacy, and backup for resource availability, provide the basis for the component
requirements.
Network operators will be
best equipped to defend their networks against cyberattacks if component
providers meet the standards outlined in the IEC 62443-4-2 subsection. While
specific features and capabilities must be added by component suppliers for
their devices to be suited for deployment on Industrial IoT networks, it is the
responsibility of network operators to make use of these features throughout
their network.
They must also keep in
mind that everyone who has access to the network is aware of the proper
procedures and regulations stated in the IEC 62443-4-2 subsection.
Every instruction outlined
in the IEC 62443-4-2 will generally yield a number of benefits that
significantly improve network security. However, failing to adhere to the
guidelines might have damaging effects, making the network less secure and
leaving the door open to cyberattacks.
Services offered by Moxa
Moxa has developed the
EDS-4000/G4000 Series, which follows the software development lifecycle
guidelines of IEC 62443-4-1, as one of the world's first IEC 62443-4-2
certified Ethernet switches. Moxa's industrial networking devices bring
customers a wide range of options for enhancing their network security.
Easy World is Moxa's official distributor in
the Middle East. For any further information, please contact us via sales@eworldme.com.






